64 gb of ecc ram (48gb cache used by zfs) with 2tb drives (3 of them)
Moonrise2473
I have similar speeds on a truenas that I installed on a simple i3 8100
One day I had a power outage and I wasn't able to mount the btrfs system disk anymore. I could mount it in another Linux but I wasn't able to boot from it anymore. I was very pissed, lost a whole day of work
it is now a non issue
IMHO it's still a big issue that might lead to data loss to someone else. The Windows client should be hardcoded to refuse syncing in onedrive folder.
~~Someone should reproduce this in a VM and open a GitHub issue~~
Edit: they already know this since a couple years, and the same happens on MacOS https://github.com/nextcloud/desktop/issues/4276
Illegal but tolerated: just think to all the Chinese companies thriving on Facebook ads sales
They crack down on it only when they need to punish a specific target/person
When you enter China, you have to run their application on your phone to fill the immigration form. Way more convenient compared to the paper slip, right? 😉
It's this https://apkpure.com/zhong-guo-ling-shi/com.gov.mfa
Luckily, you don't need to install full malware but only medium malware, there's a way to run it as a web app inside tencent WeChat by scanning a special qr code.
I run this stuff inside insular because tencent is tencent and even on fully patched Android 15 without any file access permission they still manage to drop fingerprinting files disguised as images in /pictures/.gs_fs0
For connecting to my servers, technically ssh on standard ports isn't blocked (otherwise it would hurt their bots, no?) but I don't want to show my server IP address, so I use a hysteria2 proxy hosted on a Oracle VM in the Japan datacenter. There are services like doggygo that rent access to those proxys for literal pennies (like $2 per month) but payment need to do with alibaba's alipay or tencent wepay which is ultra traceable (linked to Chinese id+Chinese bank account+Chinese phone number) and very stupid. Honeypot?
There are reports of evil maid attacks where a secret service agent poses as room cleaner in your hotel room and tampers with your laptop when you're away, but for normal people this seems unlikely. Keep your electronics with you at all times, always use a VPN, check hashes of executables if really need to run them (better not) and you're going to be ok
This could be an option but a little cumbersome to keep updated perhaps?
Debian on auto update with minimal packages lasts for years
Another option that I'm using is this:
- I do a encrypted backup with Borg on a separate drive on my server
- On my work desktop PC, Windows, at boot it connects via ssh and syncs that Borg backups on a new HDD that I purchased and installed, one way sync, silently and without prompts (We are a small business and I am allowed to do that, if you're not allowed to do that it could be your parents PC)
- Success syncs are pinged to healthchecks.io which emails me if after too many days (configurable) the sync hasn't been completed
- Errors are also sent to healthchecks.io
- Company group policy settings then keeps my backup server automatically updated
Using the Yuzu case for guidance, dumping encryption keys, regardless of the source of those keys, is illegal
This is false, as the case is non existant, because it has been settled out of court. It has to be proven in court that is illegal, as there's no law that says that dumping the keys from my own hardware that i paid with my own money is illegal.
At $12/terabyte/month it seems pretty expensive for media collection (I mean: family photos are irreplaceable but generic video?)
Other options are to use "glacier" tier S3 which is cheap to rent but ultra expensive to recover (but hopefully you won't need that)
Or just put a pi+HDD hidden somewhere at work/parents and copy to that
Nice try, openai bot (/s)
Raid wasn't designed for data safety but to minimize downtime. Just swap the drive an continue operating the server seamlessly. Full backups are still required as the chance of complete failure isn't zero

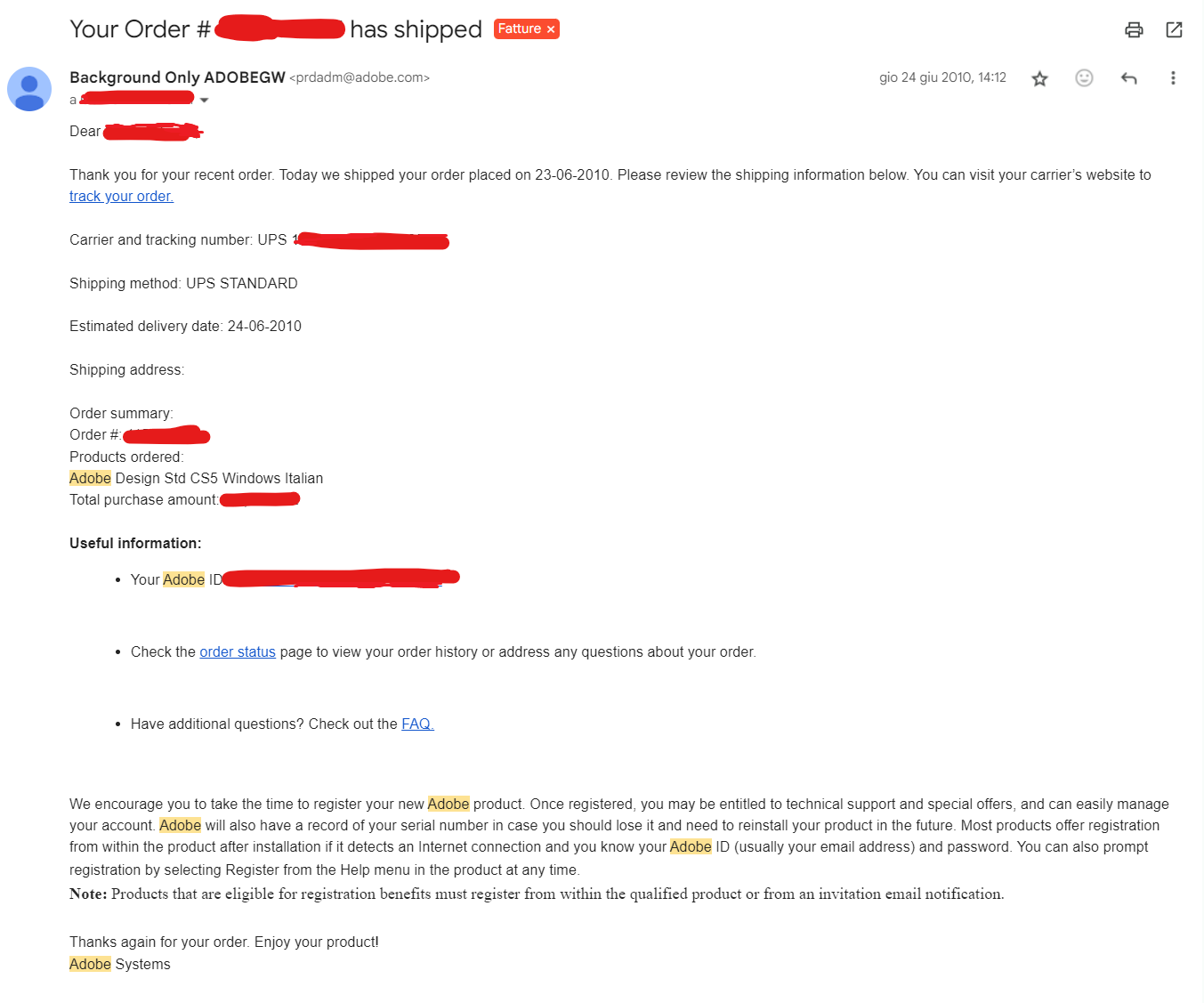
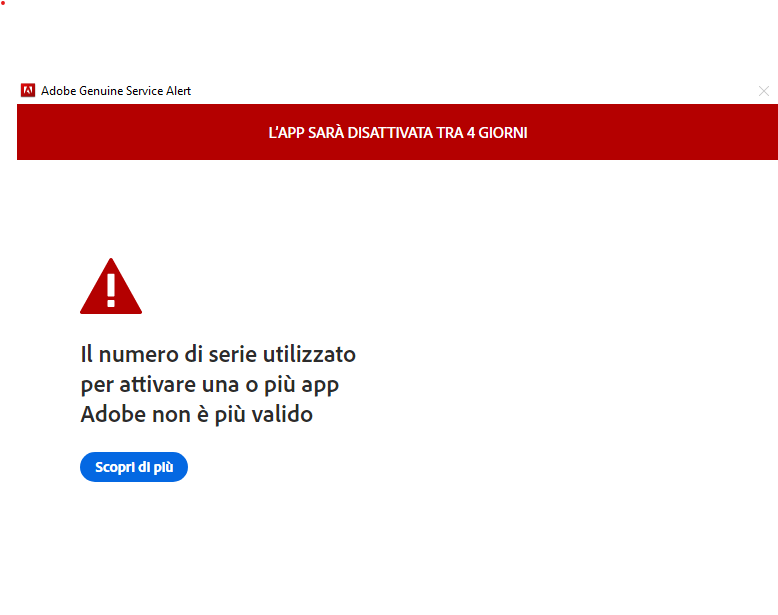
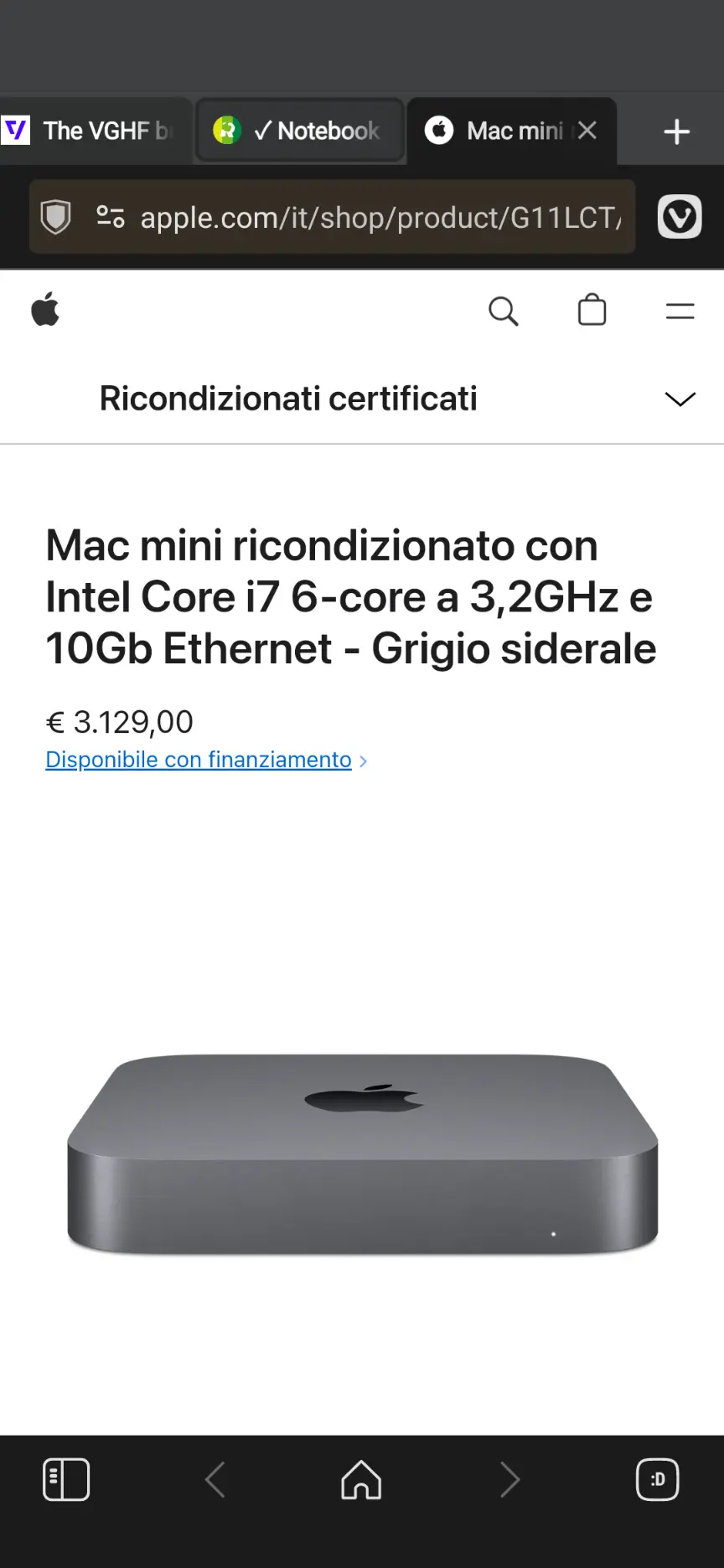
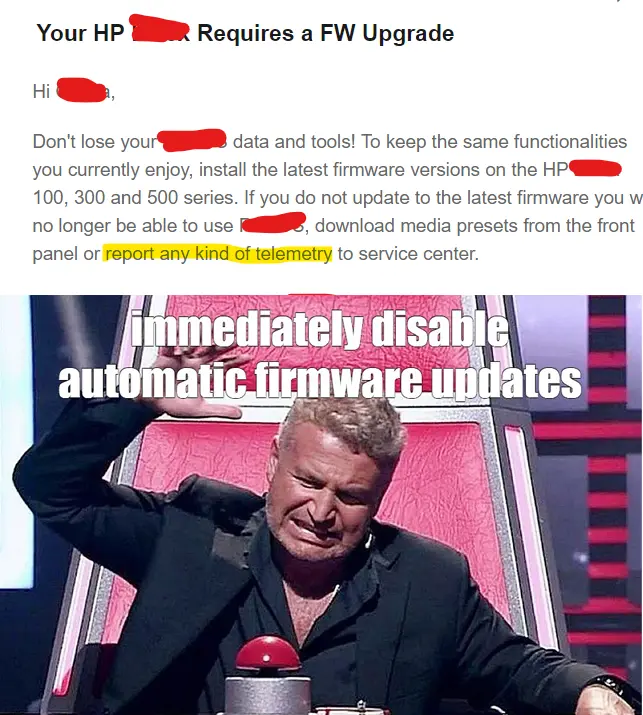
I think 5 years ago, on Ubuntu