437
this post was submitted on 02 Sep 2024
437 points (97.8% liked)
Linux
63274 readers
456 users here now
From Wikipedia, the free encyclopedia
Linux is a family of open source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991 by Linus Torvalds. Linux is typically packaged in a Linux distribution (or distro for short).
Distributions include the Linux kernel and supporting system software and libraries, many of which are provided by the GNU Project. Many Linux distributions use the word "Linux" in their name, but the Free Software Foundation uses the name GNU/Linux to emphasize the importance of GNU software, causing some controversy.
Rules
- Posts must be relevant to operating systems running the Linux kernel. GNU/Linux or otherwise.
- No misinformation
- No NSFW content
- No hate speech, bigotry, etc
Related Communities
Community icon by Alpár-Etele Méder, licensed under CC BY 3.0
founded 6 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
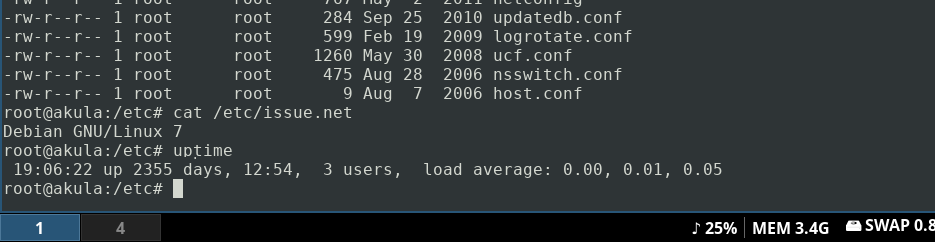
Because security.
It's behind a firewall. The only thing exposed to the outside is port 22 - and only pubkey login too.
And gee dude... It's been running for 18 years without being pwned 🙂
It hasnt been pwned so far
For that matter, it hasn't been ransomwared. There are so many ways to hide a compromise.
How do you know?
There's a file called /pwnedornot and it contains "no, you're safe bro"
Mine does
And it's not like it contains any sensitive information. I'm sure all your emails are just friendly correspondence with your pen pal.
I'd still maybe build a modern OpenSSH package.
There's been an awful lot of RCEs in the past two decades and uh, if that's rawdogging the internet, I'm honestly shocked you haven't been hit with any by now.
Eh, building anything modern on a system that old would be painful I bet.
Maybe you could use https://github.com/openssh/openssh-portable since that’s meant to be portable. I’d certainly would give it a try if I didn’t want to bother trying to upgrade that system. Then again, trying to upgrade it through the releases to a modern Debian might be fun too.
How do you know? Do you constantly monitor running processes, performance and network connections?
sorry, but what kind of email server listens only on SSH?
The most secure ones
How do you know? OpenSSH is pretty good but it isn't impenetrable. Especially for almost 10 years.
Did you really only use it when you were home? If you used it outside the firewall then port 25 must have been open also.
I used to run my own server and this was in the early 90s. Then one day, perusing the logs I realized I was not smart enough on the security front to even attempt such a thing. It was quickly shut down and the MX record moved to an outsourced mail provider.
Very very aware.
So you had another mail server elsewhere that port forwarded port 25 via port 22 to your internal mail server's port 25.
I take it that outside mail server was secure.
That's an impressive setup.
How does the mail come in tho bro? Or is your mail server just a client machine?
Maybe its for communication between family members
Where is the mail server getting incoming mail from?
Stop nuking comments pussy
That's not what a SSH is. A ssh tunnel only allows traffic after a successful SSH authentication.
Most 'hackers' are just mid tier (mediocre) IT level types who rely on existing exploits floating around in the wild. It'd probably be hard to find any still in circulation for such an old system.
We're not talking about some punch card COBOL machine he jimmy rigged with network access, it's an old Debian Linux box with SSH enabled.
It's not like Metasploit would have a tough time finding unpatched vulnerabilities for it...
What makes it a even bigger target is the fact that it is a mail server
Unless it's for SMTP only, it's probably a back end sever to some other front facing box, or service, that has IP addresses whitelisted for email.
I'm pretty sure I read one of his comments elsewhere talking about tunneling everything over SSH, so I assume that's what he meant, but I could be mistaken.
Regardless, using an EOL distro as an internet facing SSH server that's 8 years behind on SSH updates, is probably a bad idea.
It isn't the "hackers" you should worry about. Its the nation states that take over huge numbers of machines.
If the NSA (GCHQ here in the UK) want my emails they're getting it either way, I'm not able to stop nation states
I was more referring to foreign countries and cyberwarfare. Like it or not counties have now realized cyberattacks can be very devastating. A compromised server may very well be used for all sorts of purposes that many are probably not ok with.
As a private person, defending against nation threat actors is impossible. And not only as a private person, but even as a medium sized company.
You just need to not be the easy target. You don't need outrun the bear you just need to be ahead of whatever Joe is doing