Can we be neighbors?
Selfhosted
A place to share alternatives to popular online services that can be self-hosted without giving up privacy or locking you into a service you don't control.
Rules:
-
Be civil: we're here to support and learn from one another. Insults won't be tolerated. Flame wars are frowned upon.
-
No spam posting.
-
Posts have to be centered around self-hosting. There are other communities for discussing hardware or home computing. If it's not obvious why your post topic revolves around selfhosting, please include details to make it clear.
-
Don't duplicate the full text of your blog or github here. Just post the link for folks to click.
-
Submission headline should match the article title (don’t cherry-pick information from the title to fit your agenda).
-
No trolling.
Resources:
- selfh.st Newsletter and index of selfhosted software and apps
- awesome-selfhosted software
- awesome-sysadmin resources
- Self-Hosted Podcast from Jupiter Broadcasting
Any issues on the community? Report it using the report flag.
Questions? DM the mods!
Of course! But I must advice that you will be limited to 1/0,5Gbps! 😁
I would take that any day!
Draw us a topology drawing. Please.
Forget everything that I've written, I just need to assign 6 VLAN (tagged, coming in from enp2s0) to 6 NICs (untagged to: enp9s1f0, enp9s1f1, enp9s2f0, enp9s2f1, enp10s1f0, enp10s1f1).
If the connections are already tagged as you come into the Proxmox server, then you need only to create interfaces for them in Proxmox (vmbr1, vmbr2, etc). EDIT: if you’re doing PCI passthrough of the physical NICs, ignore this step.
Then, in OPNsense, you just adding the individual interfaces. No need to assign a VLAN inside OPnsense because the traffic is already tagged on the network (per your earlier statement).
Whether or not the managed switch that has tagged each port is also providing VLAN isolation, you’ll simply use the OPNsense firewall to provide isolation, which it does by default. You’ll use it to allow the connections access to the fiber WAN gateway.
I've just edited the original post to make clear that Proxmox has nothing to do in this picture, it just is installed in the same PC where the NICs are. What I need it just assign 6 VLAN (tagged, coming in from enp2s0) to 6 NICs (untagged to: enp9s1f0, enp9s1f1, enp9s2f0, enp9s2f1, enp10s1f0, enp10s1f1).
So the PC connected to opnsense is running proxmox for it's OS? Create a bridge for each physical interface, then add a tagged interface to it for the one connected to opnsense; Eg, vmbr2 could have enp2s0.100 and enp9s1f0 as members. Just add .vlanid to the end of the interface name in the bridge settings in proxmox, and don't make the bridges vlan aware. If vmbr0 is vlan aware then just add vmbr0.100 instead of enp2s0.100 With that setup the server will switch packets between the vlans on enp2s0 and the other interfaces. Don't need to put any VMs on the bridges
Will add: this is using the PC like a switch, you're probably better off using an actual switch with vlan configuration instead
That's it, thanks!!! So easy!!! Thanks a lot!
I know that it would be better to use a switch, but I would need a 10Gbps (or 2,5Gbps, do they exists) switch with 2 sfp+ port (1 for Internet connection and the second one for the server). In this way I've just bought the 3 old NIC for 25€ and that's it. I know that they will consume way more than the switch, but how many years do I need to break even?
Well it depends on how much you pay for power and what your pc consumes at idle (or at least idling while doing networking). I’d do an analysis and a graph with excel to make sure. Many old (used) networking components can be had for a steal and will still have many years of use still left in them. Use a kill-a-watt to get an accurate account of idle pc power.
He just told you. Assign VLAN on each individual port on your switch. Done. If your switch is unmanaged, then you need a new switch to support VLANs.
There are no switches in play!
If all you want is to break out the VLANs to NICs using a Linux PC instead of a managed switch, create six bridge interfaces and put in each bridge the VLAN interface and the NIC.
This is how I would do it also, assuming you aernt passing the NICs through to VMs
I have no clue what you're talking about but feel your pain in this Stackoverflow-like thread. Accept this website as my condolences.
Stolen, bookmarked. Thank you. P.s.: Can't understand the downvotes either.
If you just want each physical interface on your server to participate in a single VLAN, set the corresponding switch port as an access port in the desired VLAN, and then configure each server interface as a normal untagged interface.
You would only do tagged frames (802.1q trunking) if you wanted to support several VLANs on the switch port.
Yes, but...how do I do that?
Some diagram would help. Are you trying to use your server as a switch?
I understand the attraction of virtualising this, but unless you want to share more than just the ISP connection, I would be providing Internet access to your neighbour’s untrusted network using a bare-metal router. Just my two cents.
Mmm...I'm notr trying to virtualize anything. I'll edit the post to make it clear.
Vmbr0 should be your VLAN aware bridge. You create this in the pve networking dashboard.
Then create vmbr0_101 (where 101 is your vlan). Also create vbmr0_102, and so on.
Assign those vmbr0_xxx to each of the VMs.

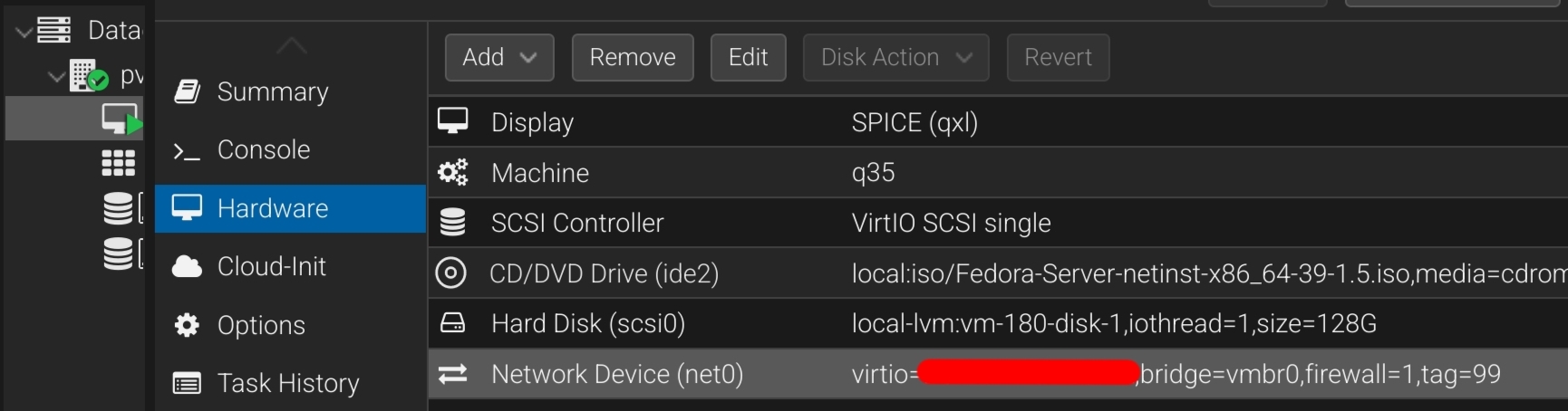
If you host all the VM's on the same box, create all the vmbr0_xyz in the pve dash, and in each VM/container>networking assign it.
I don't need to assign VLANs to VMs, I need to assign them to 6 phisical NICs (tha fact that they are installed in the same machine where there is Proxmox is irrelevant).
If Proxmox is already installed on the machine, how are you running OPNSense? If it’s not bare metal, it’s a VM, and if it’s a VM it needs Proxmox’s virtual NICs to be VLAN aware, unless you are doing PCI pass through of the entire network card.
Would they have to be VLAN aware if the switch port was already tagged AND if OP doesn’t care to consider untagged traffic ?
OPNsense is in one PC (and it only works as router/firewall), Proxmox is on another PC with all the NICs and Proxmos and it will also work as switch.
With the disclaimer that Proxmox has nothing to do with this question, I’m forced to assume this is just a networking issue that happens to use OPNsense as the router. Because of that, I must advise that you seek help from a networking-focused community. There’s no clear link to self-hosting in this post, which is required per Rule 3.
I know that you are right...sorry, but...