I'm using orbital-sync, it's not currently compatible with v6; but that's what they're working on now.
Hopefully not too long.
I'm using orbital-sync, it's not currently compatible with v6; but that's what they're working on now.
Hopefully not too long.
Nice!
Upgrade went smoothly on docker, with some neat new additions. There's new filter options in the query log. There's a bunch of new metrics under Settings > System (enable 'advanced' in the top right). And overall there seems to be many more settings available under System > All Settings. For example you can easily set the TTL for blocked responses (this was a setting burried in config files before, I was looking for it like 2 weeks ago).
If you don't use/set a password in pihole, or you set one via .env variables; you'll probably have to reset it with the command:
sudo docker exec <container_name> sudo pihole setpassword <your password here>
(empty for no password)
/edit; seems that was a temporary solution.
These env variables have changed:
Was:
webpassword=<your password>
DNS1=<upstream1>
DNS2=<upstream2>
Now:
FTLCONF_dns_upstream=<upstream1;upstream2>
FTLCONF_webserver_api_password=<your password here>
I run Borg nightly, backing up the majority of the data on my boot disk, incl docker volumes and config + a few extra folders.
Each individual archive is around 550gb, but because of the de-duplication and compression it's only ~800mb of new data each day taking around 3min to complete the backup.
Borgs de-duplication is honestly incredible. I keep 7 daily backups, 3 weekly, 11 monthly, then one for each year beyond that. The 21 historical backups I have right now RAW would be 10.98tb of data. After de-duplication and compression it only takes up 407.98gb on disk.

With that kind of space savings, I see no reason not to keep such frequent backups. Hell, the whole archive takes up less space than one copy of the original data.
ACME.sh? I love that little tool.
Cert renewal via DNS-01, independent of any other services or ports. Set it up like 7 years ago and haven't had to touch it since.
I'm having some crazy deja vu reading this 5 comment thread....
It's been a few months since I visited one of these general "how's everyone's week been" threads, but the last time I did someome else was talking about just having setup paperless, struggling to get their scanner to print to ftp, thinking about email, someone had suggested wireshark; it feels like I just re-read that exact conversion again, but they're new comments....
Freaky.
I set it up a couple weeks ago. It's alright; facial recognition works pretty well, the files are easy to manage, and setup was pretty straightforward (using docker).
Searching for images works fairly well, as long as you're searching for content and not text. Searching 'horse' for example does a pretty good job showing you your pictures of horses, but often misses images containing the word horse. Not always, but it's noticeable to me.
The mobile apps work well too; syncing files in the background as they appear, optionally creating albums based on folders. Two things I find missing though are the ability to edit faces/people in an image (you've gotta do that from a browser), and the ability to see what albums an image is in and quickly navigate to one.
It's a developing project that's well on it's way. A good choice imo.
System updates have been a faff. I'm 'ssh'ing over tailscale. When tailscale updates it kicks me out, naturally. Which interrupts the session, naturally. Which stops the update, naturally.
Have a look at Screen. You can create a persistent terminal to start your update in, disconnect (manually or by connection loss), and resume the session when you reconnect, with it having completed the update while you were gone.
Both Android and IOS usually assign a single random MAC address per network, reusing that MAC each time it connects.
I have found this to be a bit unreliable, with some devices changing their MAC after around 6 months. I tend to disable random MAC for my devices on home networks; mostly because I assign every known device on my network a fixed IP via DHCP reservations.
Fuck no; it's a part of why I finally abandoned Microsoft and went full Linux, even though I've got no experience with Linux.
It's been a fun ride; thanks for the push Microsoft.
Yeah; the lack of authentication options is a bit of a bummer if you're going to expose/share this page. There is always basic_auth in nginx or whatever proxy you're using if you really want.
I used to feel much the same way. I had a pile of bookmarks and a couple permanent browser tab groups.
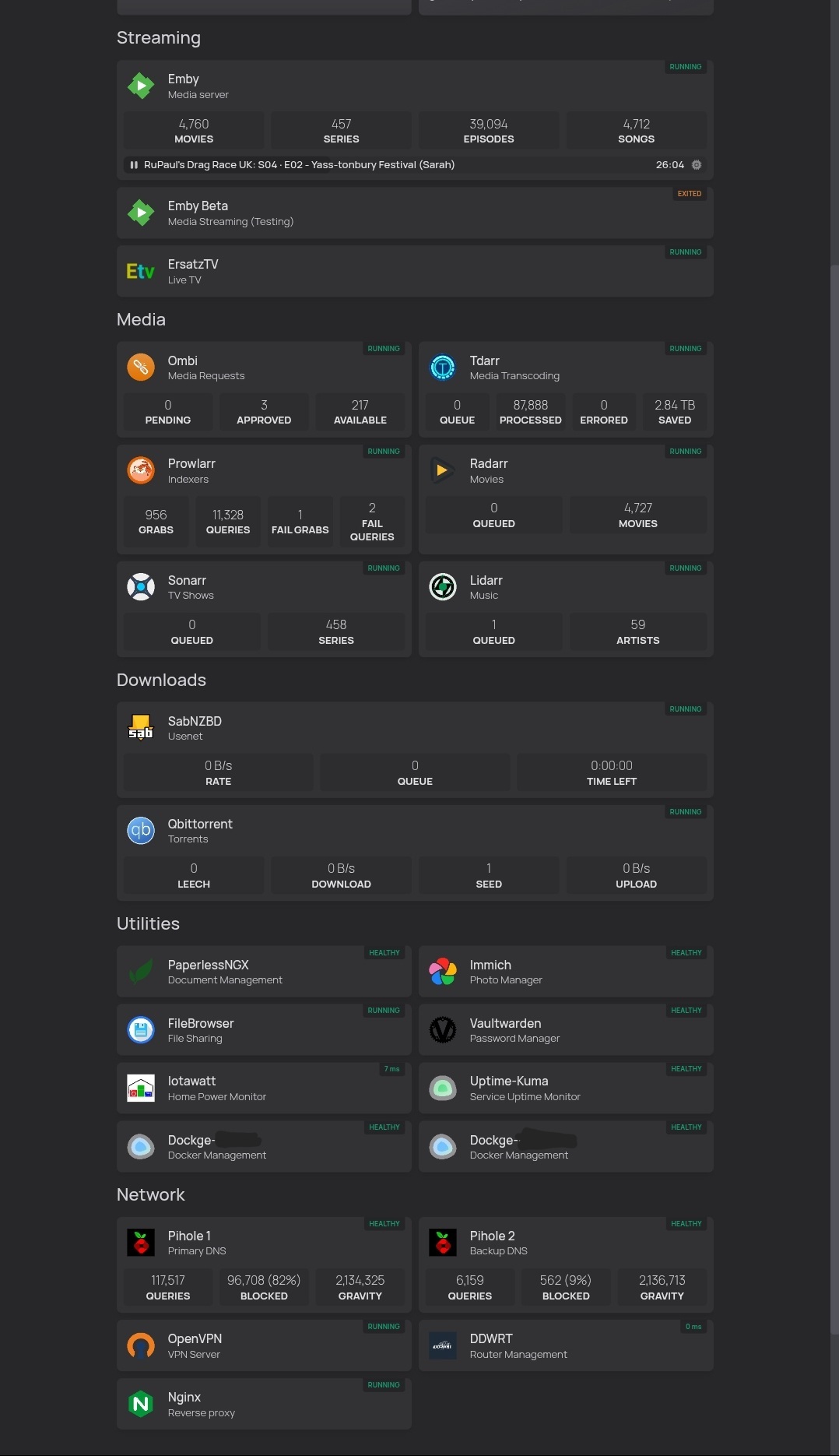
That changed when I tried out Homepage
On top of just putting all the links in one place; it was really nice to combine a bunch of information from each service to view in one place.
Now I can look at a single page and see with a quick glance; what+how many items are queued in Radarr/Sonarr/Lidarr, what's queued or errored in Tdarr, item count/time/speed in SabNZBD/Qbit, who's streaming what in Emby, and even CPU/RAM usage across multiple systems. (not pictured)
I'd recommend exploring it, I didn't think something like this was worth it until I actually tried it myself.
They've added a bit more info to the query log, when you click on individual items.
It's still not a native feature, but; You can add DOH using cloudflared, incl configuring which upstream(s) to use (you don't have to use cloudflare itself, just the tool).
There's even a docker version.