Kont is also not the most used, nicest way of saying it. “Billen” is a better match.
"Billen" is "buttocks", it's less vulgar than "kont" but it doesn't mean exactly the same thing. I think kont is also more socially acceptable with Flemish Dutch speakers than with Dutch speakers from the Netherlands.
Should also note that the word "aars" exists too. Given that they went with Arsch in German and Ass in English, it's a bit strange that they chose the word "kont" to represent Dutch.
organization that decided that a lot of Dutchified English would be changed to more Dutch terms. So is “Math” changed into “Wiskunde/Rekenen”.
Why shouldn't we use our own words to refer to things?
Also the word "wiskunde" wasn't made up by the organization you mention. It came from Simon Stevin, a Flemish 16th century mathematician.
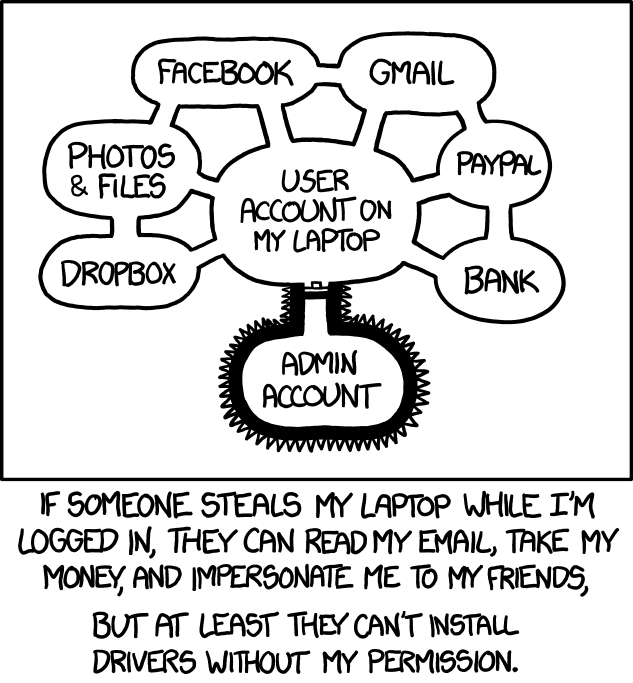
Heh the comparison also holds if you use 10=Windows 7 and 11=Windows 8
Or 10=Windows 98 and 11=Windows ME