... officials had opened a fraud investigation against the man, confirming 130 vaccinations over nine month... The man then reported an additional 87 vaccinations to the researchers, which in total included eight different vaccine formulations, including updated boosters.
Squire1039
The MLs have been shown to be extraordinarily good at statistically guessing your words. The words covered are probably comprehensive.
A speculation, https://www.phoronix.com/news/HDMI-2.1-OSS-Rejected, about HDCP, i.e. not exposing technical details as to prevent video copying, was offered.
both
Town-square when they lure you in, they own everything when they sell you ass off.
Yeah, the app data are separated and inaccessible, unless specified by the developer. Accessibility service is a separate permission, and should almost never be asked or granted, where as file/photo accesses are more common.
I agree with you. The article give a good warning about downloading applications in general, but hand-wave how they escalated from "file/photo" access to capturing your data. The recent Anatsa malware's details seem to imply accessibility service. This is a Thread Fabric article about Anatsa malware: https://www.threatfabric.com/blogs/anatsa-trojan-returns-targeting-europe-and-expanding-its-reach
From the project's page:
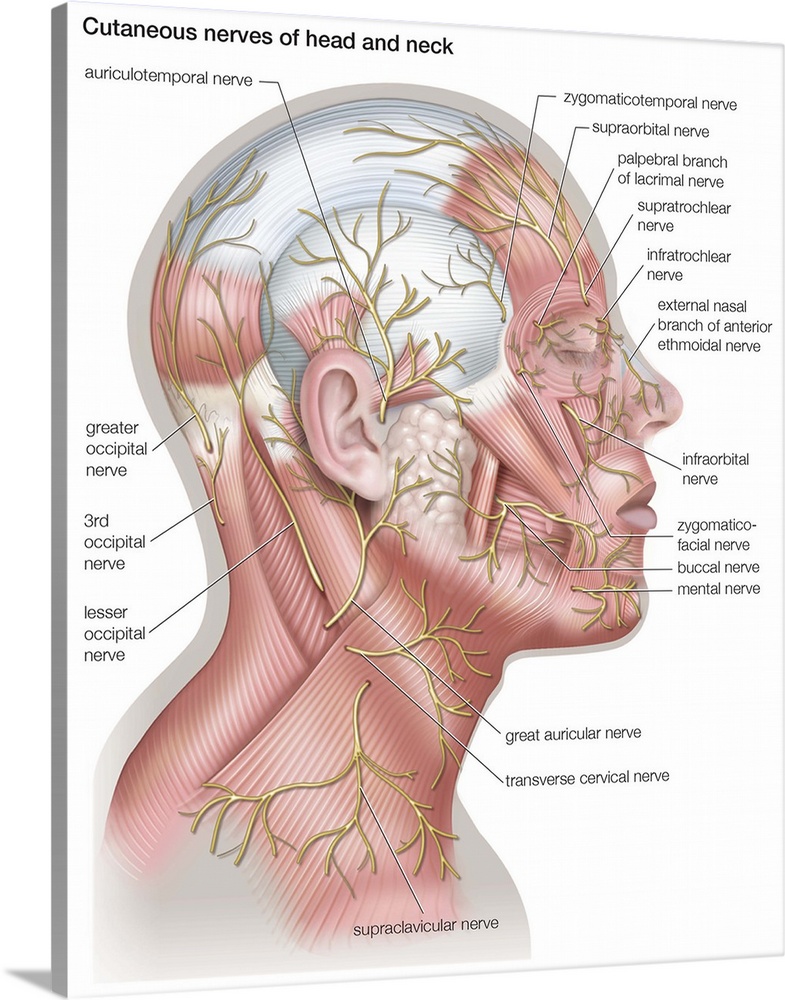
The wearable system captures peripheral neural signals when internal speech articulators are volitionally and neurologically activated, during a user's internal articulation of words.
It doesn't capture the central signal, but peripheral, most likely from the nerves running around your face and your neck used to produce speech.
No dirty thoughts! No dirty thoughts!
No, it appears to be an external headset, although it was noted that people wearing it looked like they had head injuries, but they are working on improving it so that it is less visible.
Beam me up, Scotty!
The article claims that the default assistant for a new phone is Gemini, but it seems people who responded here haven't seen it. I already have the option to switch to Gemini, which I haven't.

The canon is used to induce a radical evasive movement. Probably need lots of airbags. Looks awesome, though; would have loved it as a toy car.