For me the value of podman is how easily it works without root. Just install and run, no need for sudo or adding myself to docker group.
I use it for testing and dev work, not for running any services.
For me the value of podman is how easily it works without root. Just install and run, no need for sudo or adding myself to docker group.
I use it for testing and dev work, not for running any services.
It's the same picture.
Here you go
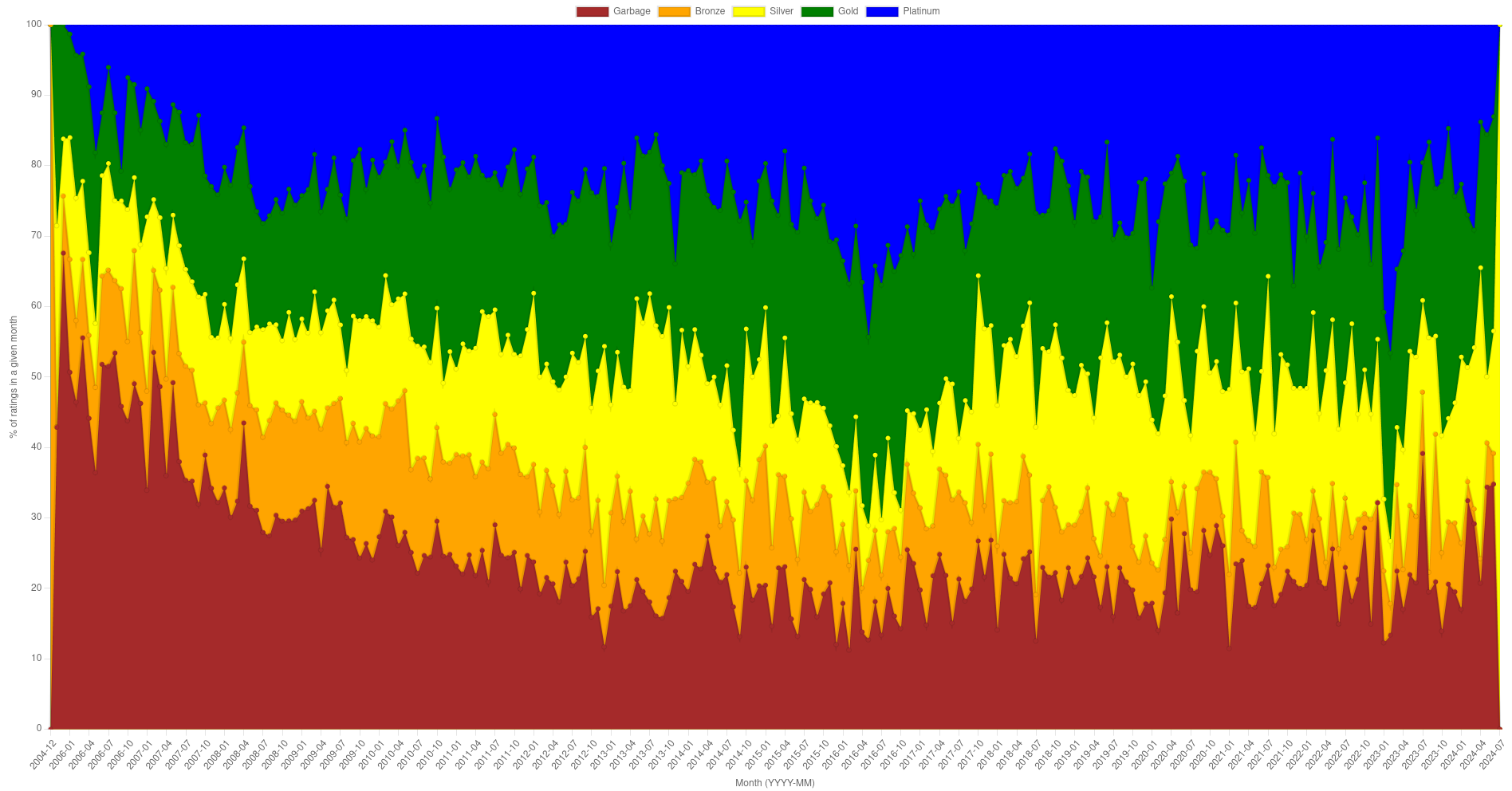
Yes it is the ratings on winehq, https://appdb.winehq.org/
And yes, an average user probably going to fire a game, figure out it is not working, and promptly go back to windows, which makes that data less accurate, but what can we do about it?
The left axis is total number of ratings of each type (Garbage, Bronze, Silver, Gold, Platinum) in a given month (not per app). For example for month 2016-07 there were
"Garbage" => 22
"Bronze" => 14
"Silver" => 13
"Gold" => 55
"Platinum" => 61
On right side is the average rating. So if I assign values to each rating:
"Garbage" => 1
"Bronze" => 2
"Silver" => 3
"Gold" => 4
"Platinum" => 5
I can get an average rating, which will be between 1 to 5.
((22*1) + (14*2) + (13*3) + (55*4) + (61*5)) / (22 + 14 + 13 + 55 + 61)
~= 3.721
Technically, containers always run in Linux. (Even on windows/OS X; on those platforms docker runs a lightweight Linux VM that then runs your containers.)
And I wasn't even using Docker.
How I lost a Postgres database:
Just did some basic testing on broadcast addresses using socat, broadcast is not working at all with /32 addresses. With /24 addresses, broadcast only reaches nodes that share a subnet. Nodes that don't share the subnet aren't reachable by broadcast even when they're reachable via unicast.
Edit1: Did more testing, it seems like broadcast traffic ignores routing tables.
On 192.168.0.2, I am running socat -u udp-recv:8000,reuseaddr - to print UDP messages.
Case 1: add 192.168.0.1/24
# ip addr add 192.168.0.1/24 dev eth0
# # Testing unicast
# socat - udp-sendto:192.168.0.2:8000 <<< "Message"
# # Worked
# socat - udp-sendto:192.168.0.255:8000,broadcast <<< "Message"
# # Worked
Case 2: Same as above but delete 192.168.0.0/24 route
# ip addr add 192.168.0.1/24 dev eth0
# ip route del 192.168.0.0/24 dev eth0
# # Testing unicast
# socat - udp-sendto:192.168.0.2:8000 <<< "Message"
2024/02/13 22:00:23 socat[90844] E sendto(5, 0x5d3cdaa2b000, 8, 0, AF=2 192.168.0.2:8000, 16): Network is unreachable
# # Testing broadcast
# socat - udp-sendto:192.168.0.255:8000,broadcast <<< "Message"
# # Worked
Here is a trick that has been tried and tested over the years: Install another distro, and use that to install Arch. This way, you can rely on an already working linux distro till your Arch install works the way you want.
TPM stores the encryption key against secure boot. That way, if attacker disables/alters secure boot then TPM won't unseal the key. I use clevis to decrypt the drive.
You have to practice switching between neovim and other editors.
You have forgotten how to use a normal editor. I am not making it up, it is a real phenomenon. Similar to when SmarterEveryDay learned to ride a backwards bicycle he forgot how to ride a normal bicycle and essentially had to re-learn it. You have to re-learn how to use a normal editor.