cross-posted to: https://sh.itjust.works/post/14114626
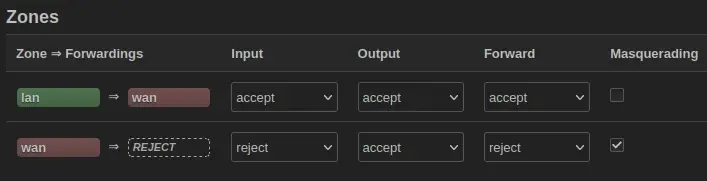
If the rule is about forwarding traffic from the lan interface to the wan interface, then why is there also a forward rule? How would inputs, and outputs make any sense if the rule is talking about forwarding? What does it mean for wan to forward to REJECT? I interperet that as saying that wan doesn't go anywhere, but that wouldn't make sense given that the router can send, and receive over the internet.
For example I would interperet the first rule as follows:
lan => wan: the conditions for which connections from the lan interface are forwarded to to the wan interface.Input: accept: the lan interface accepts all connections originating from the network (I wouldn't understand the point of setting this to be reject).Output: accept: all connections exiting the wan interface are accepted (again, I'm not sure what the point of this would be).Forward: accept: forwarding of packets from lan to wan is allowed.- Masquerade: I honestly don't know what the effect of enabling this would be. What would it mean to masquerade the
lan interface?
I tried finding documentation, and I did come across this, and this, but, from what I could understand, they didn't really answer any of my questions.
I investigated more and it seems that one can indeed perform NAT with Linux netfilter without the Masquerade action. If one knows the address of the interface, simply using the "SNAT" action with a to-address of the outbound interface will achieve the same result as using the "MASQUERADE" action, as long as the address of the outbound interface does not change.
But, this fact only matters for the actual underlying netfilter. I should have been thinking about OP's application specifically. For OpenWRT it probably does just mean Checked->NAT, Unchecked->No NAT.
That works too. Ultimately they're all NAT, that's why they're in the NAT table to begin with. Masquerade specifically is to rewrite the traffic as if it was originating from the router itself, which can be useful if you don't know which interface it'll go out, you just want it to NAT no matter where. SNAT just rewrites the source address so it's a bit less smart. There's also DNAT to rewrite where the packet will go. It's not just addresses either, you can rewrite ports too. There's also REDIRECT.
Just different ways of doing similar things, but they're all doing network address translation. For OpenWRT's purposes it is indeed what everyone thinks of a NAT, the most simple and common one. Past that a GUI becomes more of an annoyance than a feature anyway, so might as well go for scripts or at least raw iptables rules.
There's also the whole connection tracking system on top of the firewall rules. If you're clever you can make a load balancer right in iptables, since connection mappings will stick. You don't have to always rewrite it the same for every packer.